Oracle Database Network Encryption – Native
Network encryption is one of the most important security strategies. It will ensure data transmitted over the wire is encrypted and will prevent malicious attacks in man-in-the-middle form. Network encryption guarantees that data exchanged between the Application/End Users and Database System should be securely transmitted and transparently encrypted.
Since Oracle 10.2: “Network encryption (native network encryption and SSL/TLS) and strong authentication services (Kerberos, PKI, and RADIUS) are no longer part of Oracle Advanced Security and are available in all licensed editions of all supported releases of the Oracle database.
Oracle database provides below 2 options to enable database connection Network Encryption
1. Native Network Encryption
2. Encryption using SSL/TLS (Secure Socket Layer / Transport Layer Security). Click here to read more.
In this blog post, we are going to discuss Oracle Native Network Encryption.
Native Network Encryption & Data Integrity can be configured by updating the sqlnet.ora configuration file on the database server or Client side, with the following parameters. Database side encryption setup will affect all the client connections coming to the database. But client-side encryption will impose encryption only to the client where encryption parameters are set in sqlnet.ora file and other clients will remain unaffected. Native connection encryption uses Diffie-Hellman key negation algorithm. Both DB and Client session share non-secret information and based on this information generate a secret key and hereafter all communication is encrypted using this secret key. This is a classic example of Symmetric encryption where both Server and Client have the same secret key.
Database Side Parameters:-
SQLNET.ENCRYPTION_SERVER = REQUIRED
SQLNET.ENCRYPTION_TYPES_SERVER = (AES256)
SQLNET.CRYPTO_CHECKSUM_SERVER = REQUIRED
SQLNET.CRYPTO_CHECKSUM_TYPES_SERVER = (SHA512)
Client Side Parameters:-
SQLNET.ENCRYPTION_CLIENT = REQUIRED
SQLNET.ENCRYPTION_TYPES_CLIENT = (AES256)
SQLNET.CRYPTO_CHECKSUM_CLIENT = REQUIRED
SQLNET.CRYPTO_CHECKSUM_TYPES_CLIENT = (SHA512)
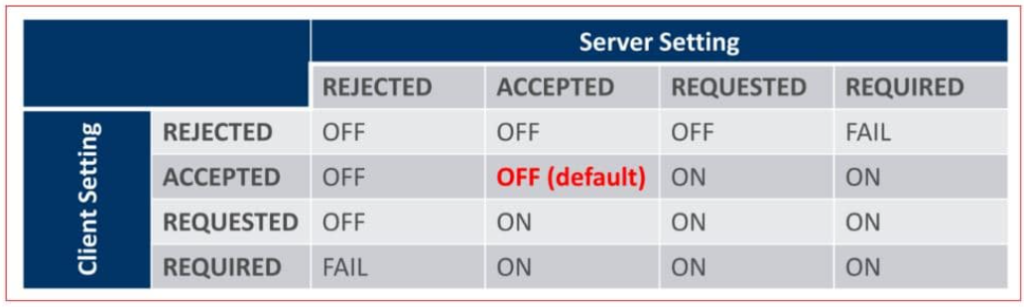
The parameter ENCRYPTION_SERVER/ENCRYPTION_CLIENT has the following options:
REQUESTED – to enable the security service if the client allows it.
REQUIRED – to enable the security service and disallow the connection if the client is not enabled for the security service.
ACCEPTED (Default)– to enable the security service if required or requested by the client.
REJECTED – to disable the security service, even if required by the client
The combination of the client and server settings will determine if encryption is used, not used or the connection is rejected, as described in the encryption negotiations matrix.
| Encryption Type | Pros | Cons |
| Native Encryption | Easy to configure | Weaker against attacks like man-in-the-middle, Server impersonation |
| No client-side changes required | ||
| No SSL/TLS certificates are required |
Connection without any Encryption parameter defines either in DB or Client Side.
As we can see from the output, the server is reporting that this connection is a standard unencrypted TCP connection. The query has also reported that the checksum and encryption services are available, but they are not currently in use. Let us now walk through how we can enable Oracle Native Network Encryption and see what is reported when encryption and checksum are enabled.
C:\Users\jkhan>
C:\Users\jkhan>sqlplus sys@app_user as sysdba
SQL*Plus: Release 11.2.0.4.0 Production on Sun Dec 19 09:47:13 2021
Copyright (c) 1982, 2013, Oracle. All rights reserved.
Enter password:
Connected to:
Oracle Database 11g Enterprise Edition Release 11.2.0.4.0 - 64bit Production
With the Partitioning, OLAP, Data Mining and Real Application Testing options
SQL> SELECT distinct NETWORK_SERVICE_BANNER from v$session_connect_info where SID = sys_context('USERENV', 'SID');
NETWORK_SERVICE_BANNER
--------------------------------------------------------------------------------
TCP/IP NT Protocol Adapter for Linux: Version 11.2.0.4.0 - Production
Oracle Advanced Security: crypto-checksumming service for Linux: Version 11.2.0.
4.0 - Production
Oracle Advanced Security: encryption service for Linux: Version 11.2.0.4.0 - Pro
duction
SQL>
Server Side Connection Encryption – No specific algorithm
We will set the parameter SQLNET.ENCRYPTION_SERVER = REQUIRED & SQLNET.CRYPTO_CHECKSUM_SERVER = REQUIRED in server sqlnet.ora file and restart listener. These server parameters will force the client to connect with encryption. And if the client fails to support encryption the connection will fail. In the below example, as you can see the client is connected with the Encryption algorithm: AES256 and Data Integrity Algorithm: SHA1.
[oracle@test-machine01 admin]$
[oracle@test-machine01 admin]$ cat sqlnet.ora
# sqlnet.ora Network Configuration File: /u01/app/oracle/product/11.2.0.4/db_1/network/admin/sqlnet.ora
# Generated by Oracle configuration tools.
# This file is actually generated by netca. But if customers choose to
# install "Software Only", this file wont exist and without the native
# authentication, they will not be able to connect to the database on NT.
NAMES.DIRECTORY_PATH= (TNSNAMES, EZCONNECT)
SQLNET.AUTHENTICATION_SERVICES= (NTS)
SQLNET.ENCRYPTION_SERVER = REQUIRED
SQLNET.CRYPTO_CHECKSUM_SERVER = REQUIRED
[oracle@test-machine01 admin]$
[oracle@test-machine01 admin]$
[oracle@test-machine01 admin]$ lsnrctl stop
LSNRCTL for Linux: Version 11.2.0.4.0 - Production on 19-DEC-2021 09:54:35
Copyright (c) 1991, 2013, Oracle. All rights reserved.
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=TCP)(HOST=test-machine01)(PORT=1521)))
The command completed successfully
[oracle@test-machine01 admin]$
[oracle@test-machine01 admin]$ lsnrctl start
LSNRCTL for Linux: Version 11.2.0.4.0 - Production on 19-DEC-2021 09:54:35
Copyright (c) 1991, 2013, Oracle. All rights reserved.
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=TCP)(HOST=test-machine01)(PORT=1521)))
The command completed successfully
[oracle@test-machine01 admin]$
C:\Users\jkhan>
C:\Users\jkhan>sqlplus sys@app_user as sysdba
SQL*Plus: Release 11.2.0.4.0 Production on Sun Dec 19 09:56:44 2021
Copyright (c) 1982, 2013, Oracle. All rights reserved.
Enter password:
Connected to:
Oracle Database 11g Enterprise Edition Release 11.2.0.4.0 - 64bit Production
With the Partitioning, OLAP, Data Mining and Real Application Testing options
SQL>
SQL> SELECT distinct NETWORK_SERVICE_BANNER from v$session_connect_info where SID = sys_context('USERENV', 'SID');
NETWORK_SERVICE_BANNER
--------------------------------------------------------------------------------
TCP/IP NT Protocol Adapter for Linux: Version 11.2.0.4.0 - Production
Oracle Advanced Security: AES256 encryption service adapter for Linux: Version 1
1.2.0.4.0 - Product
Oracle Advanced Security: crypto-checksumming service for Linux: Version 11.2.0.
4.0 - Production
Oracle Advanced Security: encryption service for Linux: Version 11.2.0.4.0 - Pro
duction
Oracle Advanced Security: SHA1 crypto-checksumming service adapter
SQL>
Server Side Connection Encryption – Specific algorithm Encryption : AES256 & Data Integrity: SHA512
In the below example we are adding two more parameters that force the client to connect with the same specified algorithm i.e Encryption Algorithm: AES256 & Data Integrity Algorithm: SHA512 only. If the client fails to support the specified algorithm then the connection will fail. As demo Oracle client version is 11.2.0.4 it’s not supporting the latest Data integrity algorithm SHA512 and hence connection fail. We can check in DB alert.log error “TNS-12649: Unknown encryption or data integrity algorithm“.
[oracle@test-machine01 admin]$
[oracle@test-machine01 admin]$ cat sqlnet.ora
# sqlnet.ora Network Configuration File: /u01/app/oracle/product/11.2.0.4/db_1/network/admin/sqlnet.ora
# Generated by Oracle configuration tools.
# This file is actually generated by netca. But if customers choose to
# install "Software Only", this file wont exist and without the native
# authentication, they will not be able to connect to the database on NT.
NAMES.DIRECTORY_PATH= (TNSNAMES, EZCONNECT)
SQLNET.AUTHENTICATION_SERVICES= (NTS)
SQLNET.ENCRYPTION_SERVER = REQUIRED
SQLNET.ENCRYPTION_TYPES_SERVER = (AES256)
SQLNET.CRYPTO_CHECKSUM_SERVER = REQUIRED
SQLNET.CRYPTO_CHECKSUM_TYPES_SERVER = (SHA512)
[oracle@test-machine01 admin]$
[oracle@test-machine01 admin]$ lsnrctl stop
LSNRCTL for Linux: Version 11.2.0.4.0 - Production on 19-DEC-2021 09:54:35
Copyright (c) 1991, 2013, Oracle. All rights reserved.
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=TCP)(HOST=test-machine01)(PORT=1521)))
The command completed successfully
[oracle@test-machine01 admin]$
[oracle@test-machine01 admin]$ lsnrctl start
LSNRCTL for Linux: Version 11.2.0.4.0 - Production on 19-DEC-2021 09:54:35
Copyright (c) 1991, 2013, Oracle. All rights reserved.
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=TCP)(HOST=test-machine01)(PORT=1521)))
The command completed successfully
[oracle@test-machine01 admin]$
C:\Users\jkhan>
C:\Users\jkhan>sqlplus sys@app_user as sysdba
SQL*Plus: Release 11.2.0.4.0 Production on Sun Dec 19 10:02:30 2021
Copyright (c) 1982, 2013, Oracle. All rights reserved.
Enter password:
ERROR:
ORA-12537: TNS:connection closed
Enter user-name:
[oracle@test-machine01 trace]$ vi alert_ucastest.log
***********************************************************************
Fatal NI connect error 12649, connecting to:
(LOCAL=NO)
VERSION INFORMATION:
TNS for Linux: Version 11.2.0.4.0 - Production
Oracle Bequeath NT Protocol Adapter for Linux: Version 11.2.0.4.0 - Production
TCP/IP NT Protocol Adapter for Linux: Version 11.2.0.4.0 - Production
Time: 19-DEC-2021 10:02:02
Tracing not turned on.
Tns error struct:
ns main err code: 12649
TNS-12649: Unknown encryption or data integrity algorithm
ns secondary err code: 0
nt main err code: 0
nt secondary err code: 0
nt OS err code: 0
opiodr aborting process unknown ospid (126749) as a result of ORA-609
Sun Dec 19 10:03:25 2021
***********************************************************************
Client Side Connection Encryption – No specific algorithm
the advantage of client side encryption is that only specific clients can be enabled for encryption and the rest of the other clients remain unaffected. Below we are removing all encryption parameters from Server side sqlnet.ora file and restart the listener. As default setting is ACCEPTED. This will enable the security service on the server side if required or requested by the client.
Server Side Change in sqlnet.ora file
[oracle@test-machine01 admin]$ cat sqlnet.ora
# sqlnet.ora Network Configuration File: /u01/app/oracle/product/11.2.0.4/db_1/network/admin/sqlnet.ora
# Generated by Oracle configuration tools.
# This file is actually generated by netca. But if customers choose to
# install "Software Only", this file wont exist and without the native
# authentication, they will not be able to connect to the database on NT.
NAMES.DIRECTORY_PATH= (TNSNAMES, EZCONNECT)
SQLNET.AUTHENTICATION_SERVICES= (NTS)
[oracle@test-machine01 admin]$
[oracle@test-machine01 admin]$
[oracle@test-machine01 admin]$ lsnrctl stop
LSNRCTL for Linux: Version 11.2.0.4.0 - Production on 19-DEC-2021 09:54:35
Copyright (c) 1991, 2013, Oracle. All rights reserved.
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=TCP)(HOST=test-machine01)(PORT=1521)))
The command completed successfully
[oracle@test-machine01 admin]$
[oracle@test-machine01 admin]$ lsnrctl start
LSNRCTL for Linux: Version 11.2.0.4.0 - Production on 19-DEC-2021 09:54:35
Copyright (c) 1991, 2013, Oracle. All rights reserved.
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=TCP)(HOST=test-machine01)(PORT=1521)))
The command completed successfully
[oracle@test-machine01 admin]$
Client-Side Change in sqlnet.ora file
D:\Oracle\product\11.2.0.4\db_1\NETWORK\ADMIN>
D:\Oracle\product\11.2.0.4\db_1\NETWORK\ADMIN>type sqlnet.ora
# This file is actually generated by netca. But if customers choose to
# install "Software Only", this file wont exist and without the native
# authentication, they will not be able to connect to the database on NT.
SQLNET.AUTHENTICATION_SERVICES = (NTS)
SQLNET.ENCRYPTION_CLIENT = REQUIRED
SQLNET.CRYPTO_CHECKSUM_CLIENT = REQUIRED
D:\Oracle\product\11.2.0.4\db_1\NETWORK\ADMIN>
D:\Oracle\product\11.2.0.4\db_1\NETWORK\ADMIN>
D:\Oracle\product\11.2.0.4\db_1\NETWORK\ADMIN>
D:\Oracle\product\11.2.0.4\db_1\NETWORK\ADMIN>sqlplus sys@app_user as sysdba
SQL*Plus: Release 11.2.0.4.0 Production on Sun Dec 19 10:27:56 2021
Copyright (c) 1982, 2013, Oracle. All rights reserved.
Enter password:
Connected to:
Oracle Database 11g Enterprise Edition Release 11.2.0.4.0 - 64bit Production
With the Partitioning, OLAP, Data Mining and Real Application Testing options
SQL> SELECT distinct NETWORK_SERVICE_BANNER from v$session_connect_info where SID = sys_context('USERENV', 'SID');
NETWORK_SERVICE_BANNER
--------------------------------------------------------------------------------
TCP/IP NT Protocol Adapter for Linux: Version 11.2.0.4.0 - Production
Oracle Advanced Security: AES256 encryption service adapter for Linux: Version 1
1.2.0.4.0 - Product
Oracle Advanced Security: crypto-checksumming service for Linux: Version 11.2.0.
4.0 - Production
Oracle Advanced Security: encryption service for Linux: Version 11.2.0.4.0 - Pro
duction
Oracle Advanced Security: SHA1 crypto-checksumming service adapter
SQL>
Reference : Oracle Doc : https://docs.oracle.com/en/database/oracle/oracle-database/12.2/dbseg/configuring-network-data-encryption-and-integrity.html#GUID-258AB895-1DFA-4A14-9D66-1645F9D5D824
This document is just for learning purpose and always validate in the LAB environment first before applying in the LIVE environment.
Hope so you like this article!
Please share your valuable feedback/comments/subscribe and follow us below and don’t forget to click on the bell icon to get the most recent update. Click here to understand more about our pursuit.
Related Articles
- Oracle Critical Database Patch ID for October 2024 along with enabled Download Link
- Oracle Critical Database Patch ID for July 2024 along with enabled Download Link
- Oracle Critical Database Patch ID for April 2024 along with enabled Download Link
- Oracle Critical Database Patch ID for April 2023 along with enabled Download Link
- Oracle Critical Database Patch ID for January 2023 along with enabled Download Link
![]()